AES Encryption
for
Radio Remote Controls and Pendants.

Here we show you how we secure our
Radio remote controls
from hackers, so that the crane can be operated safely.
So if you want to make sure that your knowledge of the current encryption technology is up to speed, you should get a lot of value from today’s content.
- AES Encryption.
- Operation of AES.
- AES Features.
- AES 128-Bit Key Size vs AES 256-Bit Key Size.
- Encryption Process.
- Decryption Processes.
- Security.
- Applications of AES Algorithm.
- Conclusion.
Introduction to AES encryption
Security is one of the essential factors in today's Digital age. Every device requires confidentiality while communicating
information. To protect data during wireless or wired communication, encryption is a common technique, which secures the data
from being hacked .
Encryption technique works by converting our information into ciphertext. This ciphertext is mainly made
up of random characters, by using a special secret key. There are many encryption techniques available to provide security
while transmitting and receiving information.
AES is one of the common techniques which is used today by public and government authorities. AES is the first and only
publicly accessible cipher data, which was approved by the United States (US) National Security Agency (NSA) in 2001.
At first, it was specifically used for protecting the topmost secret information.
An Advanced Encryption Standard (AES) uses a symmetric block cipher technique for protecting the information.
This technique is used on hardware as well as software to secure the data. It is very essential for government computer
security, cybersecurity, and electronic data protection.
An algorithm of AES encrypts every character of the data, one at a moment from the main cipher. As it uses a symmetric
algorithm, it requires the same key for encryption as well as the decryption process. Commercially, the AES algorithm
is widely used all over the globe.
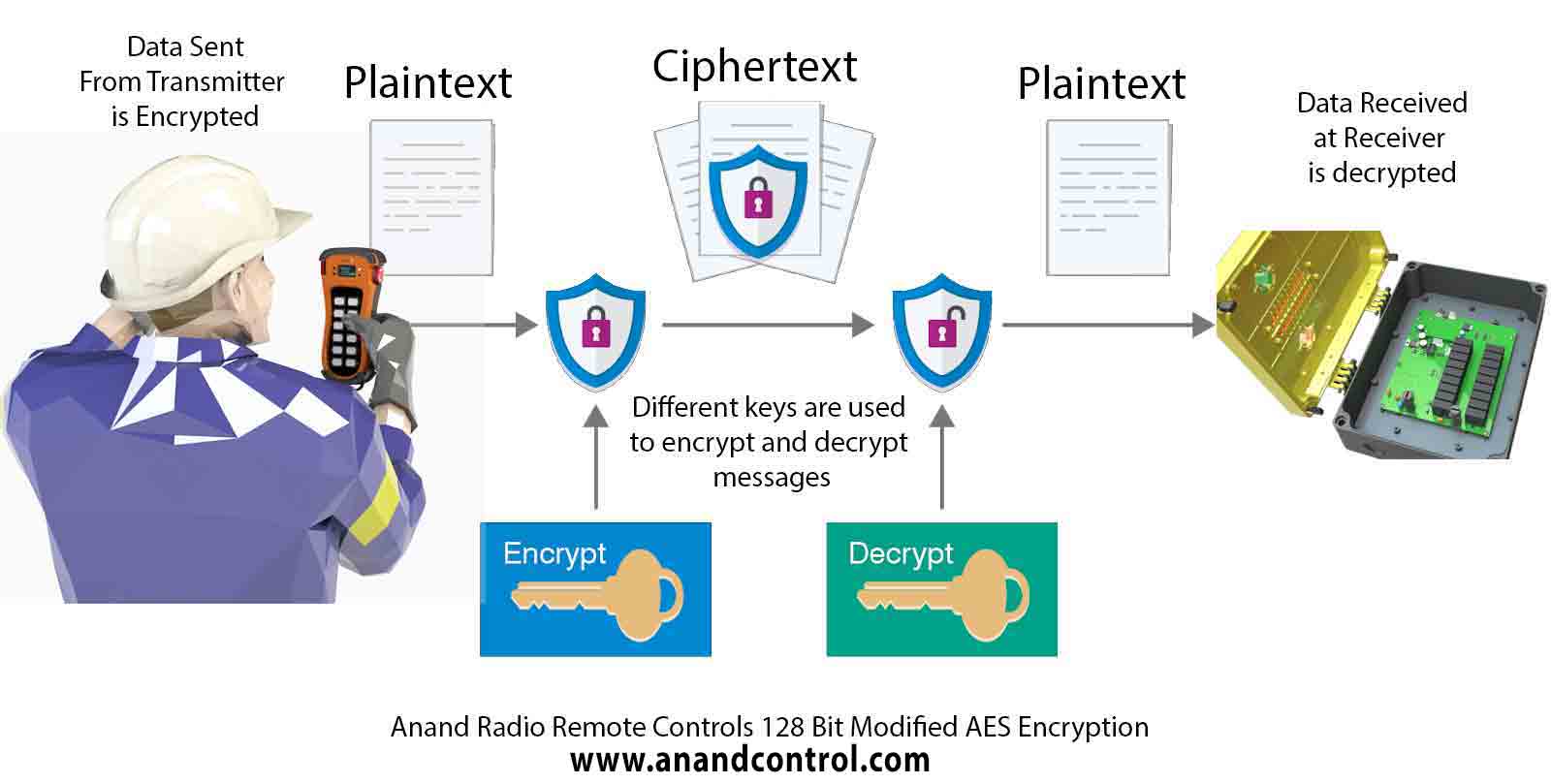
AES Process
Whenever data is sent over the network, first it is encrypted while using a secret key. As the
data gets encrypted it gets converted into a cipher text.
It is then transmitted to the desired receiver. When
the receiver gets the information that is in encrypted form, it is decrypted by using the same key
which was used during encryption procedure.
Similarly, the data gets converted into the original
form i.e. plain text.
Operation of AES
Advanced Encryption Standard (AES) is a computational process .
It is
based on a series of linked mathematical operations i.e. substitution-permutation network (SPN).
This algorithm comprises replacing some of the inputs with some particular substitutions or it shuffles
the bits around the permutations. AES algorithm performs on bytes rather than bits.
AES operates 128 bits of plaintext block as 16 bytes. Here 16 bytes are arranged in a matrix as four
rows and four columns. AES uses three types of key sizes used such as 128, 192, and 256 bits for
encryption.
As the algorithm uses a large key size, it is very robust for hackers to crack it.
When the AES algorithm uses 10 rounds encryption for a 128-bit key, 12 rounds for 192-bit keys, and
14 rounds for a 256-bit key. Each encryption round uses a different 128-bit round key.
AES Features:
- It is capable of handling 128-bit blocks by using 128, 192, and 256 bits.
- It has a competing algorithm that can resist the attack as compared to other ciphers. Security is the main important factor for the AES algorithm.
- As it has 128 bits, hence it expects more than 2128 attempts to decipher the code. This makes the AES cipher highly secure and almost impossible to hack.
- As it is released on a global basis, it’s free of cost. The algorithms were evaluated on computational and memory efficiency.
- Compare to triple-DES it is more likely faster and stronger.
- As it is a symmetric algorithm, it requires only one encryption and decryption key.
AES 128-Bit Key Size vs AES 256-Bit Key Size
- A 256-bit encryption key is more secured than the 128-bit encryption key, as it is more difficult for brute-force attacks.
- 256-bit encryption key requires more processing power as compared to a 128-bit encryption key, also it takes much time to execute. Where the power is not a concern for the end customer, then a 256-bit encryption key is the best option for them.
- 256-bit encryption key requires more processing power as compared to a 128-bit encryption key, also it takes much time to execute. Where the power is not a concern for the end customer, then a 256-bit encryption key is the best option for them.
Encryption Process
As AES algorithm operated every 128-bit of blocks into 4 x 4 bytes matrix of each 16-byte segment. The length of the keys determines the number of rounds required. Every round contains four sub- processes, the steps involved in each process as mentioned below:
-
Byte Substitution
The 16 bytes are treated as input in a fixed table. Then the result stores in 4 rows and 4 columns matrix. -
Shift Rows
The following process includes:
a) The matrix first row is not shifted.
b) The second row of the matrix is shifted by one left position.
c) The third row of the matrix is shifted by two positions to the left.
d) The fourth row of the matrix is shifted by three positions to the left.
Hence a new matrix is formed with the same 16 bytes, which composed of multiple positional changes.
-
MixColumns
A mathematical function is applied to every four-byte columns. The function takes four bytes of one column as input and provides completely new bytes as outputs that replace the original column.
The output is a new matrix of 16 new bytes. However, we should note that MixColumns steps cannot be performed in the last rounds. -
AddRoundKey
The output of the MixColumn steps matrix is considered as 128 bits and it is Exclusive-ORed with the round key.
If AddRoundKey is considered as the last round of encryption, then we will be getting encrypted data i.e. cipher text.
However, if this isn’t the last round then the result of 128 bits will again be considered as 16 bytes as the previous round. And again we have to start the round.
Decryption Processes
We have to perform inverse steps of the encryption operation as mentioned below:
-
1. AddRoundKey
We have to use a similar key which has been used during the encryption method. So, we have to expand the AES key which matches to the encryption key. Then we have to use the correct key while performing the Exclusive-OR operation. -
2. MixColumns
This is the next inverse operation, which is done by performing the multiplication of the matrix. This multiplication operation reverses the initial operation. -
3. Shift Rows
This step is similarly inversely to the ShiftRows as performed during the encryption process. Except these rotations are made from right instead of left. -
4. Byte Substitution
The last operation of the round is SubBytes operation. We have to perform the inverse operation of the S-Box table.
Advanced Encryption Standard (AES) Algorithm Better Than DES (Data Encryption Standard) Algorithm
- DES algorithm uses a 56-bit key for securing the information. While the AES algorithm can use up to 256-bit keys for securing data. As it becomes more robust for hacking.
- DES algorithm is sometimes used for its backward compatibility feature.
- AES algorithm is mathematically more efficient than the DES algorithm.
- AES encryption is significantly much faster than the DES algorithm, as the AES algorithm provides low latency and high throughput.
Advanced Encryption Standard (AES) Algorithm Better than RSA (Rivest-Shamir-Adleman) Algorithm
- AES uses a single key for encryption and decryption processes. However, RSA uses two keys, the public key for the encryption process and the private key for the decryption process. Commonly RSA is used only when there are two separate end-users.
- AES has a wide range of applications such as database encryption, storage encryption, Internet, disk drives, etc. However, RSA has often used for websites and VPN (Virtual Private Network) connections.
- RSA encryption is good for securing the data during the transfer process. However, its performance is low as compared to the AES encryption algorithm
- The combination of both algorithms will provide the best solution for the end-users. This can be achieved if we generate a temporary AES algorithm key for protecting the RSA encryption. This will offer better secured data.
Security
- AES algorithm is more secure than any other algorithm for encryption data. We have to just secure the AES encryption key, as it can be vulnerable if the key gets leaked to the hacker.
- Even the security experts have considered the AES algorithm as the safest one, which resists against the brute-force attacks.
- We just have to consider the large key size during encryption as it cannot be cracked easily, even for the high-speed processors. As the AES algorithm offers three key sizes of 128-bit, 192-bit, or 256-bit with each uses the 128-bit blocks.
- The length of the AES algorithm key determines the strong level of encryption. With the 256- bit key size, a hacker needs to try the attempt of 2 265 different combinations to achieve the correct one. For high-security purposes, the AES algorithm is one of the best algorithms.
Applications of AES Algorithm
-
Voice Communication
In today’s life, the secured mode is an important factor for preventing information from getting leaked out. As people are continuously using wireless phones to communicate with each other. These types of technology are using Voice over Internet Protocol (VoIP). This needs higher strength encryption, as many peoples use it as a mode of communication. Here the AES algorithm is the best option for the encryption. As its longer encryption key will secure the data more effectively. -
Network Appliances
Network appliances are a market leader, which helps people to stay connected with each other at a remote distance. Hence it is the root of communication of transferring data from end to end users, the chances of cyber-attack on the network are very high. To prevent the attack of these hackers, the AES algorithm is the best option for the network. While sending the file over the network, it will encrypt the data with the help of a special key. The receiver will decrypt the data with that similar key. Hence the middle man can get access to the original data. -
Virtual Private Network (VPN)
VPNs are most commonly used in industrial sectors. As it protects the direct connection between the users and enterprise networks. The cost of these is very high as it requires both hardware and software support. A leased-line is a very secure one and private. However, it is very expensive, as everyone cannot get a private line. Here we can use the AES encryption algorithm. We can encrypt the VPM traffic which is on the public line, which will make this cost-effective. -
Secure Socket Layer (SSL)
Secure Socket Layer (SSL) protocol offers a security for Internet browser-based transaction. In this case, encryption is the most important factor for making an online payment. AES encryption algorithm is the best option for securing the payment mode. Not even a single person will want to take a risk regarding payment mode. Hence, in this case AES is very essential factor for encryption algorithm. -
Internet
The Internet has become a daily basic need for each and every person. Every day every single person shares their information, data, images, files, etc. over the internet. For staying connected with each other internet has become a major factor. However, some hackers will try to leak the information from the end-users. Hence the information which is shared over the internet needs to be secured. We can use the AES encryption algorithm to secure our data. AES comes into a picture while transferring the files through HTTPs connection. We can also secure the Wi-Fi router through encryption so that an unauthorized person cannot access it. It is commonly combined with WPA2 protocol, which gets further termed as AESWPA2. -
Storage Devices
We want to prevent the data from unauthorized access. We can use the AES algorithm in this scenario. During the encryption method, a Random Number Generator (RNG) generates the 256-bit key, which is passed to the engine. The AES engine encrypts the original information into encrypted data and then it is sent to the storage devices. As the one who has the key can only have access to the storage devices. If the user wants to access the data from storage devices, the AES engine will decrypt the cipher text and give access to the original data.
Conclusion
- In present situations, information security is very essential. Each and every person wants its data to be secured. There is a huge demand for this type of algorithm at the industry level. As each company wants it to be confidential. AES is the best option for such types of needs. It will provide secured data with this simple procedure.
- Hence, the AES algorithm is widely adopted across the world. It is the most robust algorithm which a hacker can attack the information easily. This algorithm provides better security as compared to other algorithms. AES encryption algorithm is better than other algorithms as it offers a high level of security and high throughput.
- AES encryption algorithm offers a customized solution against unauthorized access, illegal actions, and other security threats. Till now, there are no practical cryptanalytic attacks against AES encryption algorithm has been discovered.
- Also, the AES encryption algorithm offers in-built flexibility of key length, which offers a degree of ‘future-proofing’ against the progress in the ability to perform exhaustive key searches.
Anand Systems Engineering is an Indian manufacturer of Radio Remote Control systems for Cranes and Hoists with a Goal of modernizing Indian Engineering.
Follow us on YouTube.